AT88SC0808C-SI データシートの表示(PDF) - Atmel Corporation
部品番号
コンポーネント説明
メーカー
AT88SC0808C-SI Datasheet PDF : 13 Pages
| |||
AT88SC0808C
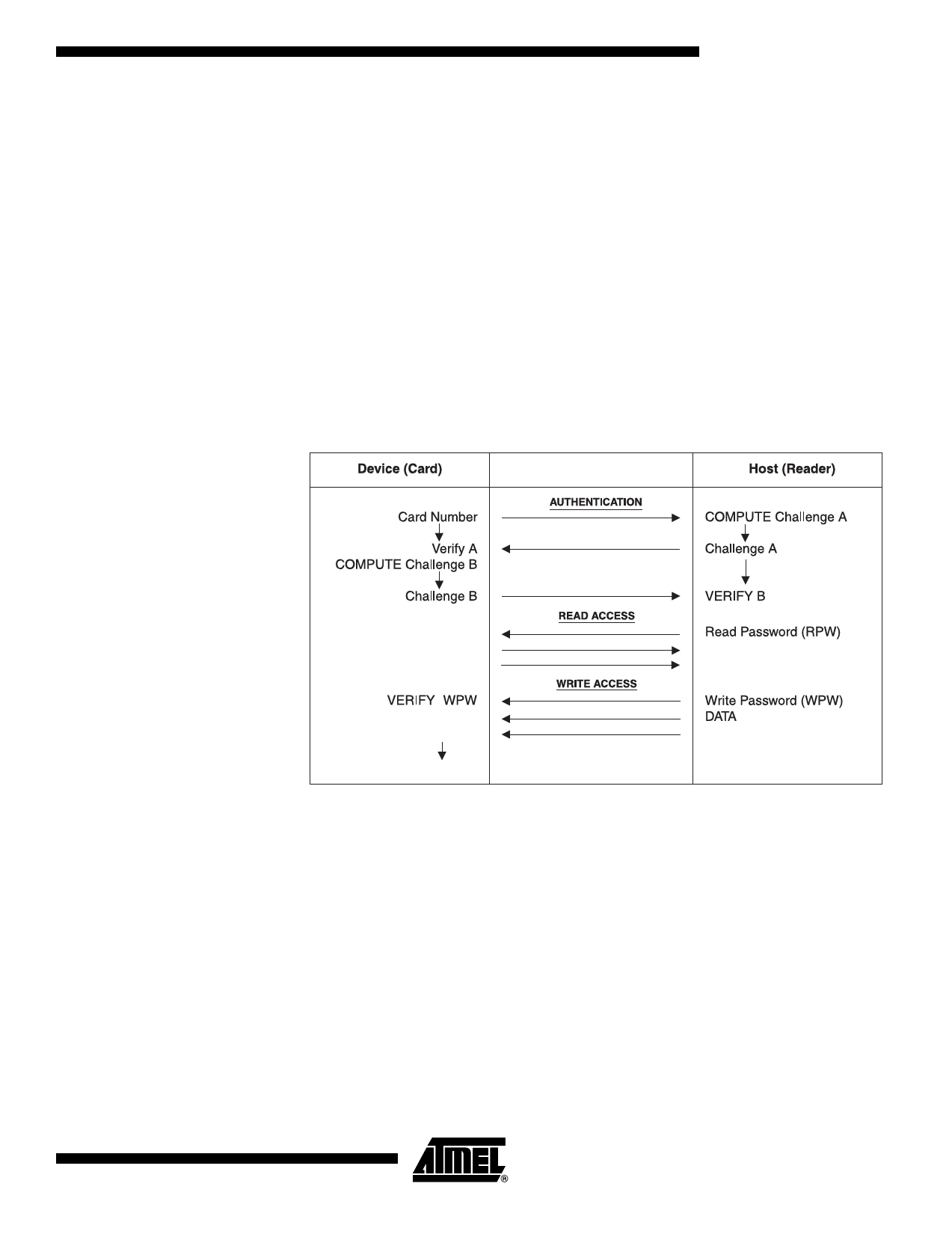
Password Verification
Passwords may be used to protect read and/or write access of any user zone. When a
valid password is presented, it is memorized and active until power is turned off, unless
a new password is presented or RST becomes active. There are eight password sets
that may be used to protect any user zone. Only one password is active at a time, but
write passwords give read access also.
Authentication Protocol
The access to a user zone may be protected by an authentication protocol. Any one of
four keys may be selected to use with a user zone.
The authentication success is memorized and active as long as the chip is powered,
unless a new authentication is initialized or RST becomes active. If the new authentica-
tion request is not validated, the card loses its previous authentication and it should be
presented again. Only the last request is memorized.
Note:
Password and authentication may be presented at any time and in any order. If the trials
limit has been reached (after four consecutive incorrect attempts), the password verifica-
tion or authentication process will not be taken into account.
Figure 4. Password and Authentication Operations
Checksum
2024BS–SMEM–10/02
VERIFY RPW
DATA
Checksum (CS)
VERIFY CS
VERIFY CS
CS
Write DATA
The AT88SC0808C implements a data validity check function in the form of a check-
sum, which may function in standard, authentication or encryption modes.
In the standard mode, the checksum is implemented as a Modification Detection Code
(MDC), in which the host may read a MDC from the device in order to verify that the data
sent was received correctly.
In the authentication and encryption modes, the checksum becomes more powerful
since it provides a bidirectional data integrity check and data origin authentication capa-
bility in the form of a Message Authentication Code (MAC). Only the host/device that
carried out a valid authentication is capable of computing a valid MAC. While operating
in the authentication or encryption modes, the use of a MAC is required. For an ingoing
command, if the device calculates a MAC different from the MAC transmitted by the
host, not only is the command abandoned but the mode is also reset. A new authentica-
tion and/or encryption activation will be required to reactivate the MAC.
7